Understanding 5G Network Security: Safeguarding the Next Generation of Connectivity

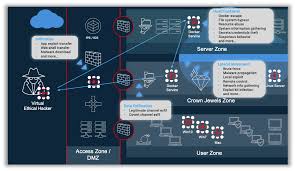
The rollout of 5G networks marks a new era in telecommunications, promising unparalleled speed, reduced latency, and the ability to connect billions of devices worldwide. This transformation is expected to drive innovation across industries, from autonomous vehicles to smart cities, and healthcare. However, with this leap forward in technology comes a critical challenge: 5G network security. As 5G becomes the backbone of our digital infrastructure, ensuring its security is paramount. In this blog, we'll delve into the key aspects of 5G network security, the challenges it presents, and strategies to safeguard this vital technology. The New Security Landscape of 5G Networks 5G networks differ fundamentally from their predecessors. While previous generations of cellular networks were primarily centralized and hardware-driven, 5G introduces a more decentralized and software-based architecture. This shift, while enabling greater flexibility and efficiency, also creates new security vul...