Understanding Breach and Attack Simulation: Strengthening Your Cybersecurity Posture
In today’s rapidly evolving digital landscape, cyber threats have become increasingly sophisticated, posing significant risks to businesses of all sizes. Organizations must adopt proactive strategies to defend their digital assets effectively. One such approach that has gained considerable attention is Breach and Attack Simulation (BAS). In this blog, we'll explore what BAS is, why it’s crucial for modern cybersecurity, and how it can benefit your organization.
What is Breach and Attack Simulation?
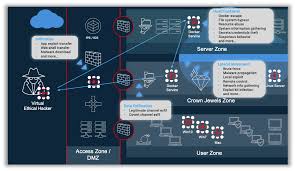
Breach and Attack Simulation (BAS) is a cybersecurity technique that allows organizations to test their security defenses by simulating real-world attack scenarios. Unlike traditional security assessments that rely on manual penetration testing or vulnerability scanning, BAS tools continuously and automatically simulate various attack vectors, providing a comprehensive view of an organization’s security posture.
These simulations can include a wide range of attack techniques, such as phishing, malware injection, lateral movement within a network, and more. The goal is to identify weaknesses before actual attackers can exploit them, enabling organizations to address vulnerabilities promptly.
Why is BAS Important?
Proactive Defense: Traditional security methods often react to threats after they’ve already caused damage. BAS, on the other hand, allows organizations to stay ahead by identifying and mitigating vulnerabilities before they can be exploited by malicious actors.
Continuous Assessment: Cyber threats are constantly evolving, and so should your security measures. BAS provides continuous monitoring and testing, ensuring that your defenses are up-to-date and capable of withstanding the latest attack techniques.
Cost-Effective: While manual penetration testing can be costly and time-consuming, BAS tools automate the process, making it more affordable and accessible. This allows even smaller organizations to maintain a robust security posture without breaking the bank.
Detailed Insights: BAS provides detailed reports on the effectiveness of your security measures, highlighting specific areas that need improvement. This level of insight is invaluable for security teams looking to optimize their strategies.
How Does BAS Work?
BAS platforms use a combination of automated tools and real-world attack scenarios to test your organization’s defenses. Here’s a step-by-step overview of how it typically works:
Simulation Setup: The BAS platform is configured to simulate various attack scenarios, such as phishing campaigns, malware distribution, and network intrusions.
Execution of Simulations: The platform executes the simulated attacks, mimicking the behavior of real cybercriminals. These simulations are designed to test different layers of your security infrastructure, from email gateways to firewalls and endpoint protection.
Monitoring and Analysis: As the simulations run, the BAS platform monitors how your security systems respond. It identifies which attacks were blocked, which succeeded, and where the vulnerabilities lie.
Reporting: After the simulations are complete, the platform generates a detailed report. This report provides insights into your organization’s security posture, highlighting weaknesses and offering recommendations for improvement.
Remediation: Armed with the insights from the BAS report, your security team can take targeted actions to strengthen your defenses. This may involve patching vulnerabilities, reconfiguring security controls, or providing additional training to employees.
Benefits of Implementing BAS
Enhanced Security Awareness: By regularly simulating attacks, your organization can stay aware of the latest threats and ensure that your defenses are up to the task.
Improved Incident Response: BAS helps you identify weaknesses in your incident response procedures, allowing you to refine them and respond more effectively to real attacks.
Regulatory Compliance: Many industries require organizations to conduct regular security assessments. BAS can help you meet these requirements and demonstrate compliance with regulations like GDPR, HIPAA, and PCI DSS.
Reduced Risk: By proactively identifying and addressing vulnerabilities, BAS reduces the risk of a successful cyberattack, safeguarding your organization’s reputation and assets.
Conclusion
In a world where cyber threats are constantly evolving, organizations cannot afford to be complacent. Breach and Attack Simulation offers a proactive and cost-effective way to stay ahead of cybercriminals, ensuring that your defenses are robust and ready for any attack. By continuously testing and improving your security posture, you can minimize the risk of breaches and protect your organization’s valuable data.
Investing in BAS is not just about preventing attacks—it’s about empowering your organization to face the future with confidence. As cyber threats continue to grow in complexity, the ability to anticipate and neutralize them before they cause harm is a game-changer for any business.
Ready to strengthen your cybersecurity posture? Consider implementing Breach and Attack Simulation today.



Comments
Post a Comment