Understanding Diameter Signaling Firewall: Securing the Core of Telecom Networks
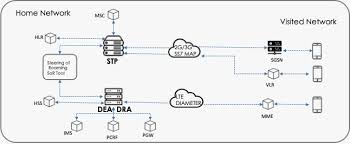
In an era where telecom networks are increasingly vulnerable to sophisticated cyber threats, protecting the signaling layer is paramount. Diameter, a core protocol in 4G and 5G LTE networks, plays a critical role in managing user authentication, billing, and service access. However, without adequate protection, this protocol can be a gateway for hackers to access sensitive data, disrupt services, or launch denial-of-service attacks. This is where the Diameter Signaling Firewall comes in, acting as a security layer to safeguard telecom infrastructure. Why Diameter Signaling Needs Protection Diameter signaling is vital to the smooth operation of telecom networks, enabling interconnectivity and communication across global networks. But due to its complexity, it is also susceptible to several security risks, such as: Location Tracking : Attackers can exploit Diameter messages to locate users, infringing on privacy and potentially leading to targeted attacks. Denial of Service (DoS) : ...





